In this guide we focus on the prerequisites and steps needed to onboard on prem servers to Azure Arc.
In order to connect your systems to Arc, there are a few options to choose from, check out the options available to you using the below link:
https://learn.microsoft.com/en-us/azure/azure-arc/servers/
In this Solution Guide we will focus on the “At scale” option “Connect Windows Machines using Group Policy”
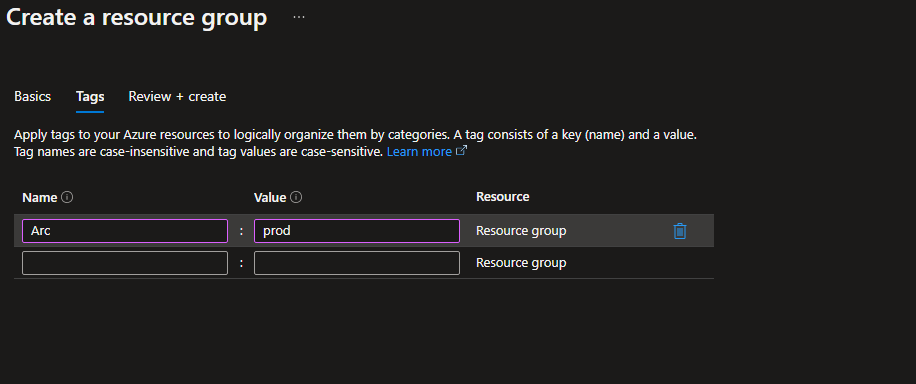
First off, lets start by creating a Resource Group which will contain all of the Arc onboarded devices and artifacts created within the guide:
Don’t forget to tag your resources!
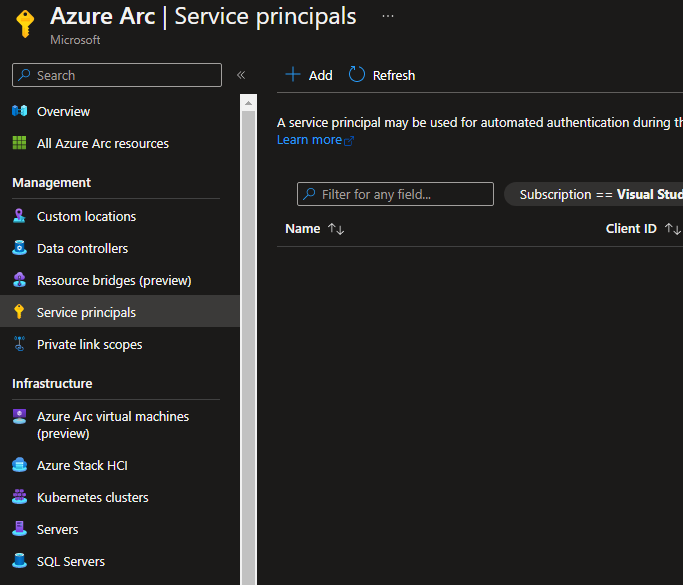
Now that your Resource Group has been created it’s time to create the Service Principal which will be used to onboard your devices.
Navigate to the Azure Arc pane in the Azure Portal, and select Service Principals under the Management Tab
Click Add, you should now be presented with the New Azure Arc service principal wizard.
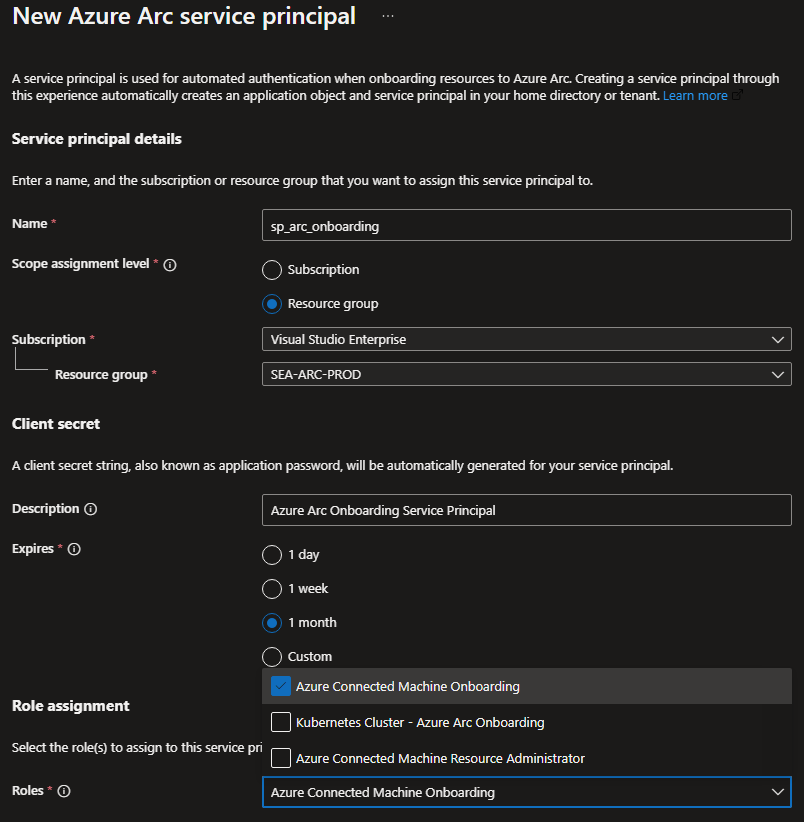
Enter the following information:
Name for your Service Principal,
Scope Assignment (In this guide we will limit the permissions to the Resource Group created earlier),
Subscription,
Client Secret Name and Expiry date,
and most importantly the permissions needed, select Azure Connected Machine Onboarding
then hit create.
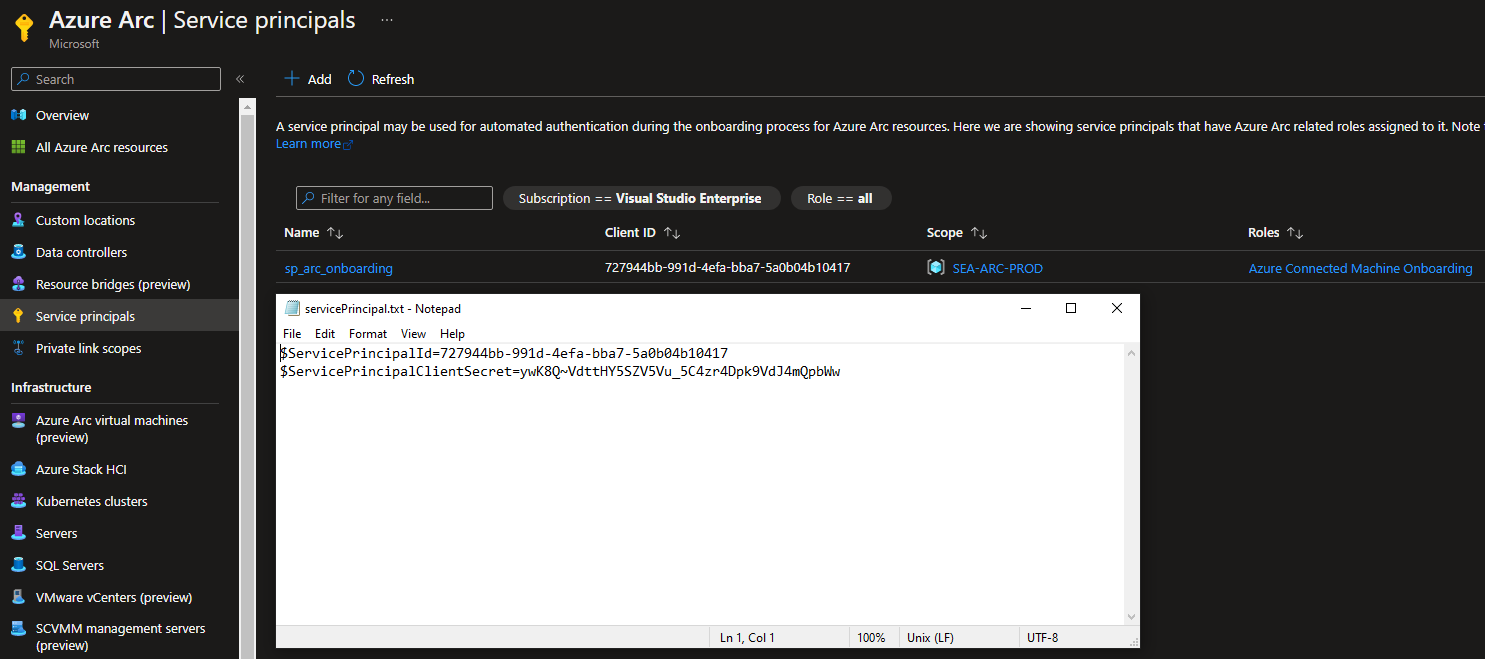
Your Service Principal is now being created:
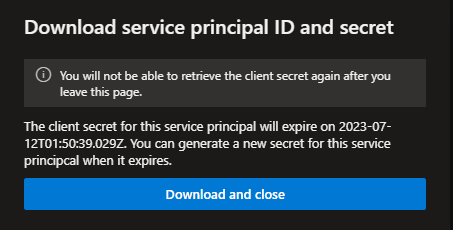
You will now be presented with the Download and close option, save the file which contains your ClientID and Secret for your Service Principal as you will need this later.
Make sure to keep the below information safe! For this demo the below Service Principal has been deleted for security purposes.
Next we need to download the GPODeploy script and it’s prerequisite files, head over to GitHub and grab the ArcEnabledServersGroupPolicy file:
https://github.com/Azure/ArcEnabledServersGroupPolicy/releases/latest/
Extract the zip file from GitHub and save it to a temporary location on your Domain Controller, the GPO creation needs to be executed on the Domain Controller itself.
Suggest to save it to a temp location such as C:\temp\
Before we can deploy the GPO we need to download and copy the Connected Machine Agent MSI file to a file share which is accessable from the devices you are about to onboard.
It is not sugested using your Domain Controller for this, but rather to use a File Server share where your member servers have read access to the share.
Download the MSI file and save it to your file share: https://aka.ms/AzureConnectedMachineAgent
Once saved we can navigate back to your Domain Controller. Open up PowerShell ISE and navigate to the temp location of the DeployGPO.ps1 files.
Here we can substitute all the information we have created so far to the GPO creation script, Namely:
Domain FQDN – Your Domains FQDN
ReportServerFQDN – The FQDN of the server share
ArcRemoteShare – The file share name
ServicePrincipalClientId – The Azure Arc Onboarding Service Principal id saved to text earlier
SubscriptionId – Your subscription Id
Resource Group – The RG created earlier in this guide
Location – The Location of the RG created earlier
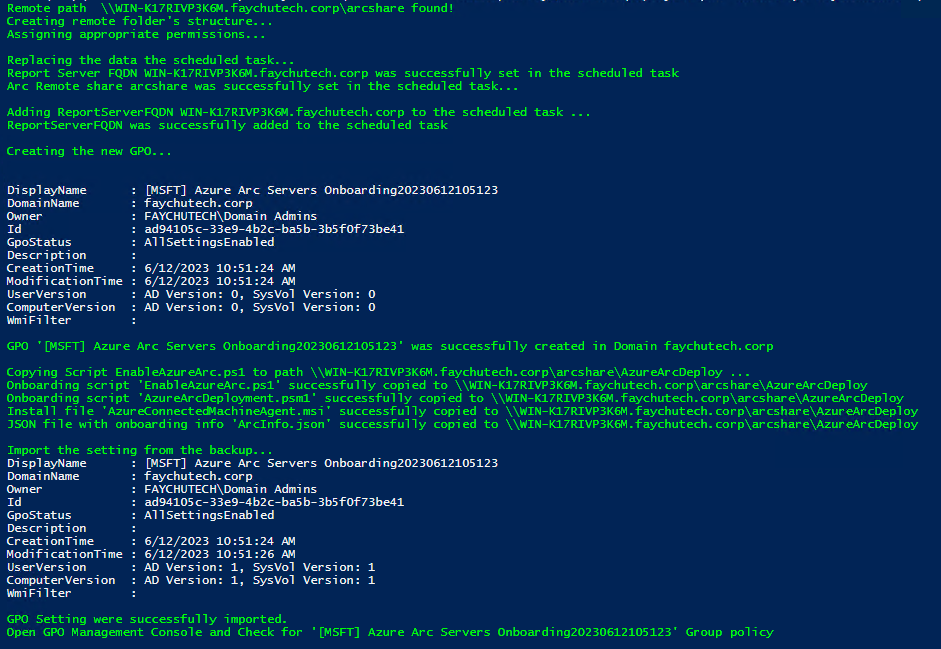
Once you have added your information, click start and the GPO will be automatically created:
Your output should be similar to the below output of the script:
With this your GPO has been created. You can link this GPO as you would any other in your day to day operations.
Some points to note, it is highly advised to limit the Security Filtering to a Security Group which only contains computer objects which you would like to pilot.
Once the behaviour has been confirmed to be satifactory the scope can be extended to more devices
Once a device has been linked you should see 2 log files in the c:\temp\ of the device, namely:
Azcmagentinstallationlog.log and AzureArcOnboarding.log
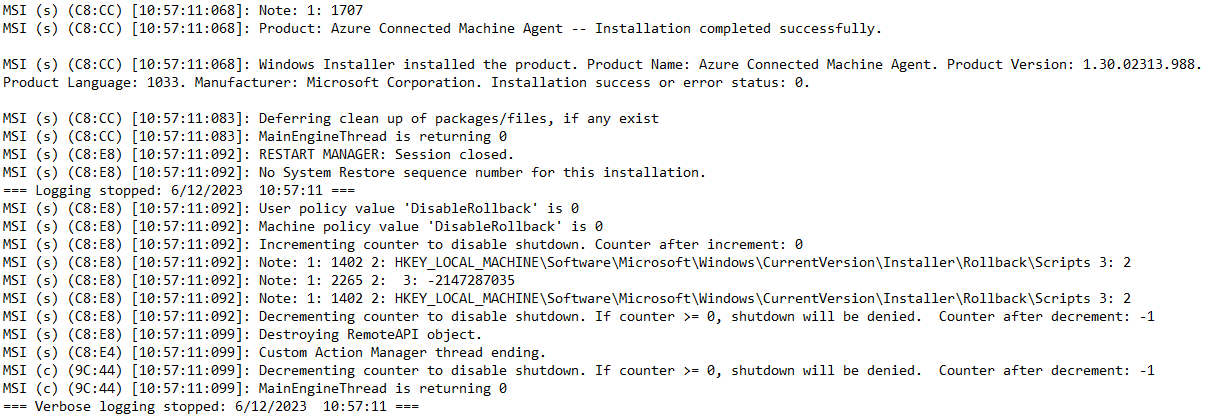
The first contains the installation logs for the Azure Connected Machine Agent, you should see the successful deployment information as below:
The second log contains the onbaording status of the device:
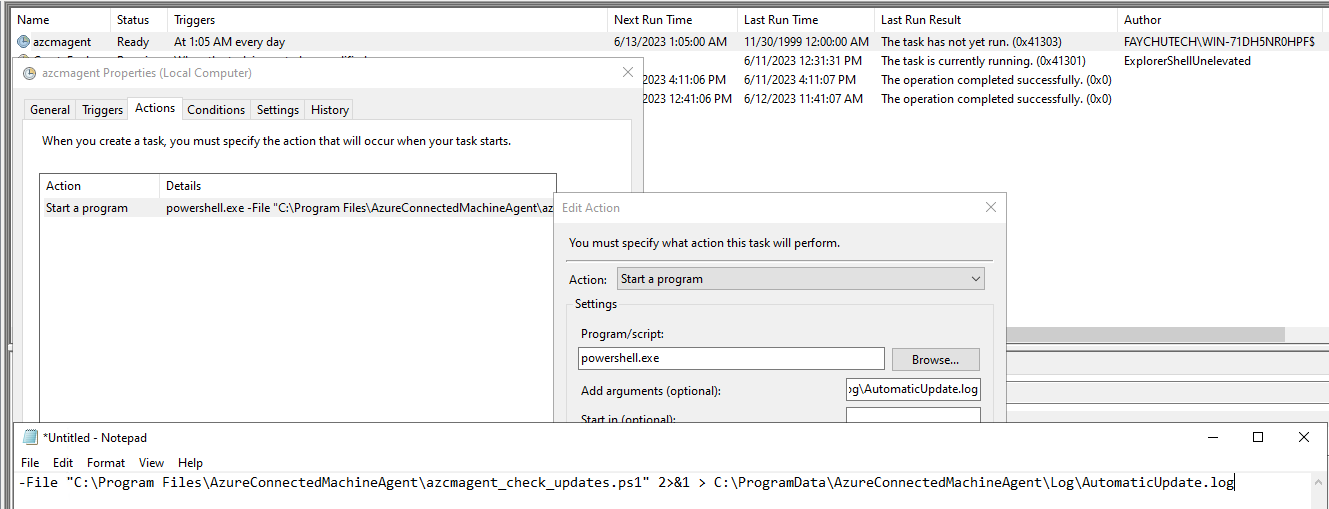
It is also worth noting that with onboarding devices in the following manner, a task schedule will also be created on each device being onboarded to manage automatic agent updates:
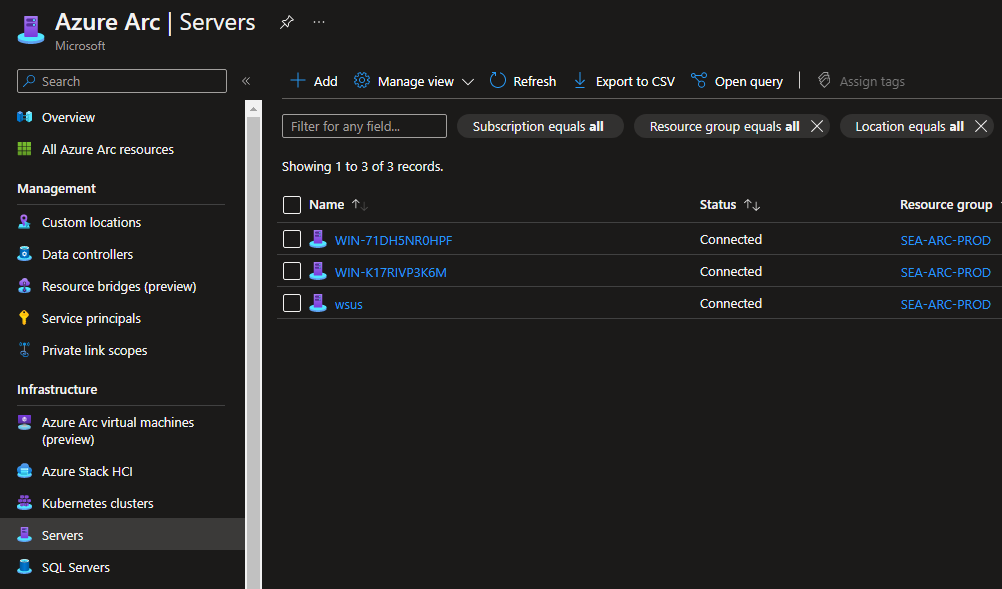
Head over back to the Azure Portal and you should now see your devices being onboarded and listed under the Servers tab under Infrastructure.
Hope this guide was helpful, happy onboarding!
In the next Solution Guide we will focus on Update Management for Azure Arc Enabled Devices!